
Security and PBX Telephony

IT security has been and continues to be a major concern for almost any business. News of high-profile businesses being hacked and sensitive customer data being leaked continue to hit the headlines, causing potentially significant damage to the business’ reputation and bottom line. Although many firms take steps to secure their IT systems, it can be a totally different story when it comes to their IP telephony network. Yet an IP-PBX system is just as vulnerable as other systems on a computer network, even more so in that many firms don’t even realize that a problem exists. Due to the nature of IP telephony, the phone system needs to be connected to the internet, which provides a route for hackers to access the IP-PBX.
While VoIP phone systems offer many advantages such as advanced call functionality and flexibility over traditional TDM, it is precisely these advantages that can also be used against it. In order for businesses to protect their IP telephony systems, they need to understand how their systems are vulnerable, how this can be exploited, and the steps they can take to secure these systems. In order to gain access to the telephony system, hackers simply need the password of the device they are targeting. In order to gain this password and successfully compromise an IP-PBX system, hackers will identify an IP extension on the network, and then bombard that device with different passwords in the hope that one of them will be right. Although this sounds like a long shot, many users don’t change their passwords from the default setting. Also, hackers can send thousands of passwords to an extension in just a couple of seconds. In many cases, it doesn’t take long for the hackers to guess the correct password and login to the IP-PBX system.
Once a hacker has access to the system, there are many ways in which they can disrupt the IP telephony network and potentially cause the business to lose large sums of money. One of the most common attacks, and indeed one of the most damaging, is when professional criminals tie an entire call center to the compromised network connection, routing thousands of calls over the one connection in a short period of time. Depending on how the IP-PBX routes its calls, and how regularly the company receives its bills, this activity can sometimes continue for months before being discovered, running up an astronomical telephone bill.
While weak passwords are one of the primary ways for hackers to take advantage of a poorly protected system, a lack of encryption in an IP-PBX infrastructure can also leave the doors wide open to other types of malicious activity. For example, because of the computerized nature of IP telephony, it is not a difficult task to secretly record internal calls. Rather than having to install a physical device, calls can simply be recorded using the right software. Often, this kind of threat can come from an employee inside the organization, making it difficult to protect against. If a company is using an unencrypted VoIP protocol, then there is no barrier in place to stop calls from being recorded. Even if the threat doesn’t come from an employee, for outside groups with an interest in recording a company’s telephone conversations, a trojan could be used to install the recording tool.
So what can be done to secure your IP PBX?
To secure an IP-PBX system, there are several steps companies should take. Firstly, administrators need to keep a close eye on the system to monitor for any signs of an attempted attack and act quickly to ensure that successful ones are addressed at an early stage. As mentioned earlier, one of the major reasons that IP-PBX systems are compromised is because hackers are able to easily break into a system that uses weak passwords. More often than should be the case, the password won’t be changed from the default password or will be changed to something easy to remember, such as the company name or “password”. Capitalizing letters and Including numbers and symbols can increase the security of a password significantly, making it much more difficult for a hacker to crack. However, most users don’t want to come up with a password that they can’t remember, but for the IT administrator, it becomes a difficult task to ensure that employees use a secure password. At Vodia, we’ve realized that this is a major issue for businesses, and have a password security measure built into our Vodia IP-PBX under system security.
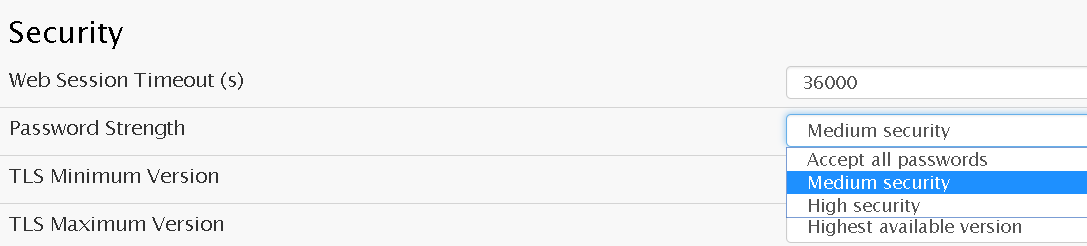
Administrators are given the opportunity to set a minimum strength level for user passwords. At the lowest setting, any password can be used. At the middle and high levels, the password chosen is given a score based on the combination of letters, numbers and symbols it contains, and any that don’t reach the required score are rejected. This can sidestep the challenge of ensuring that everyone is using a secure password, and allows administrators to upgrade the security of the IP-PBX infrastructure with the click of a button.
Even with strong passwords protecting every extension on the IP network, hackers will still try to break through a system’s defenses. Since they can try so many passwords in a short period of time, it is worth it to them to try an attack as the chances are that eventually, they will guess the correct password. For a business, this presents a very real risk, as it is difficult and time-consuming to constantly monitor the IP telephony system for attempts at illegal access. To combat this, Vodia has an email alert system that lets administrators set a limit for the number of unsuccessful access attempts by an IP address, blocking those that reach that limit and sending an email alert to the administrator. When an attack has been successful, and the hackers start routing unauthorized calls through an extension, it is very difficult for the administrator to see that this is happening.
If legitimate users don’t notice a problem, then there is nothing to alert the administrator that the IP-PBX has been compromised. This means that the hackers have free rein to route thousands of calls through the extension, and the company only finds out when it receives a large bill from its service provider. With the Vodia IP-PBX, IP extensions can also be set up to limit the number of conversations that they can handle at any one time. Obviously, no user is going to be able to handle thousands of calls in the space of a few minutes, so this feature stops hackers from routing an excessive number of calls through a compromised extension. The danger posed by someone hacking into a system can further be mitigated by setting a credit limit for outbound calls. In Vodia’s setting, it is a simple process to enter the cost of a call, allowing the system to monitor the total number of calls placed and blocking outbound calls once this limit has been reached.
Make the change before it is too late; IP telephony is now a much bigger part of corporate communication infrastructures. And while IT security is slowly but surely getting stronger, the same can’t necessarily be said of IP telephony systems, as the administrators of these systems often don’t realize the level of the danger faced. The monetary loss that can be caused by a successful hack can far outweigh the original investment in the system. Yet the measures that need to be taken to protect the business are relatively simple and don’t require a massive investment in hardware and software.
Once the right security measures have been put into place, then administrators can drastically reduce the chances of being on the receiving end of a successful hacking attack. Of course, the right IP-PBX, such as the Vodia PBX, can make this process much easier, and ensure that the transition to a secure system is a simple and painless process. To find out more on securing your IP telephony solution, please visit https://vodia.com

