
Configuring your firewall for remote users

A firewall controls the incoming and outgoing network traffic based on an applied rule set and establishes a barrier between a trusted, secure LAN and/or WAN network(s) and the internet (not secure, nor trusted).
Vodia Networks recommends a LAN architecture where the voice traffic bypasses the firewall, as shown below:
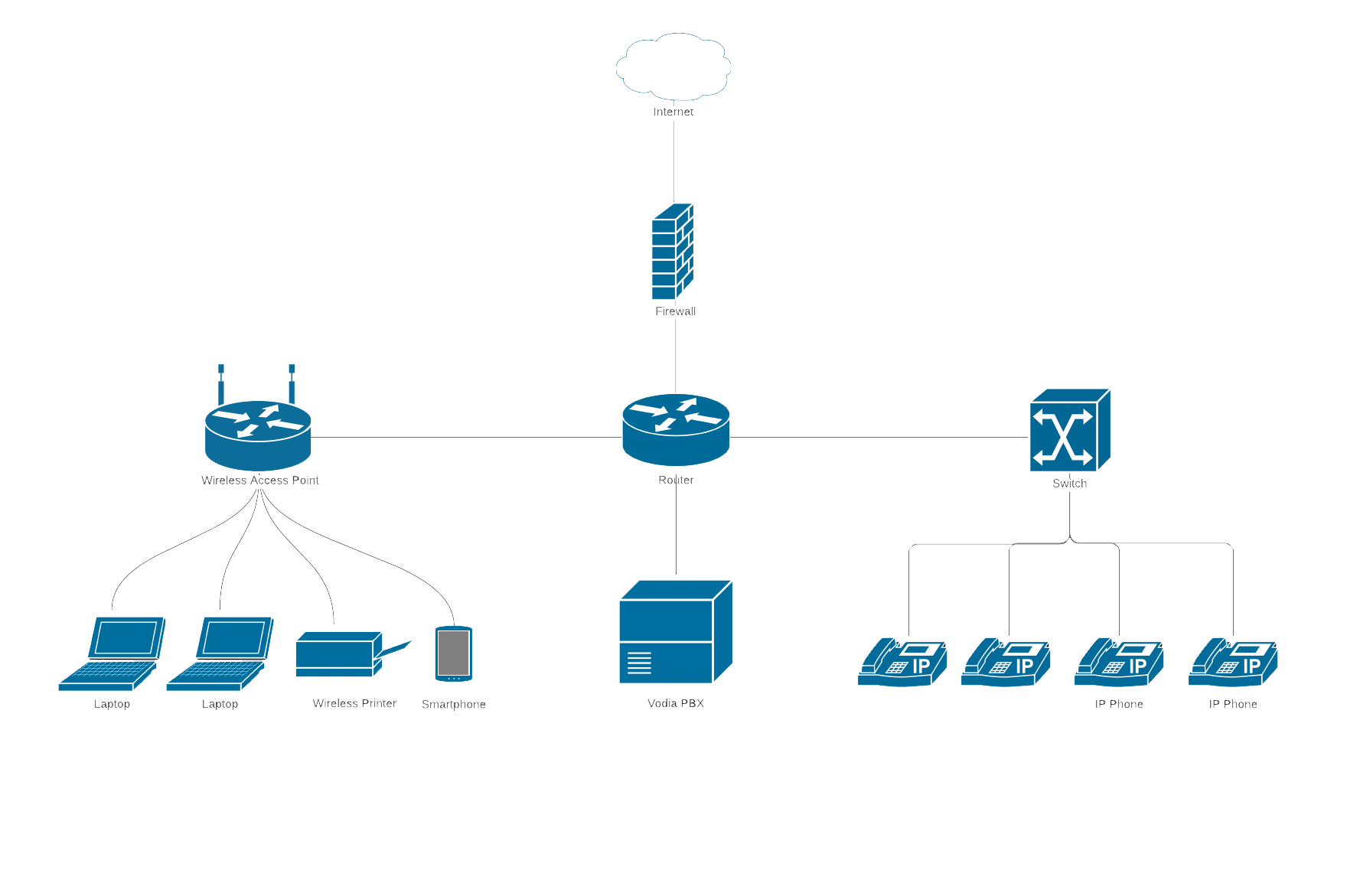
If a firewall feature is configured, it must allow the following ports to pass. If you want to connect remote users to the PBX then will need to configure the Vodia SBC settings
Allow TCP/UDP ports 5060, 5061 (for SIP)
Allow UDP ports 49152–64512(for RTP)1
Allow UDP port 123 (for NTP)
Allow TCP port 80 (for HTTP)
Allow TCP port 443 (for HTTPS)
Vodia PBX SBC
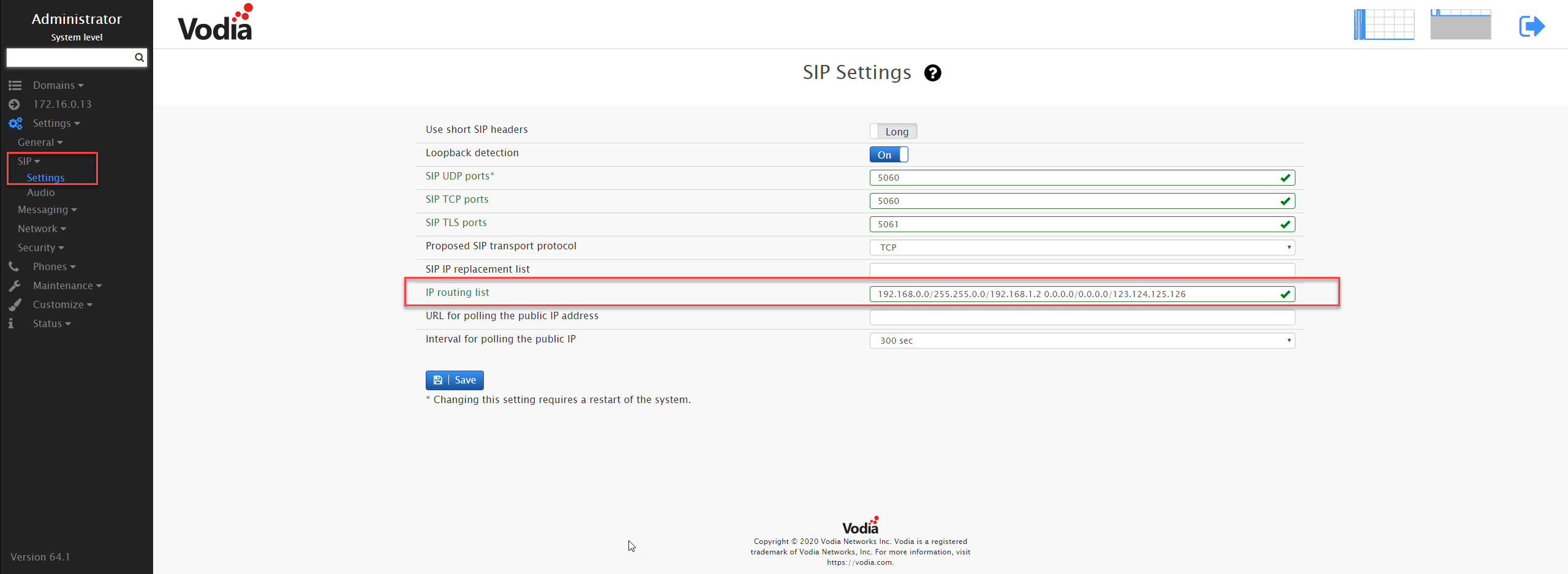
In order to make the PBX show the public IP address, you need an entry that matches "every other IP address". In other words, the netmask must be 0.0.0.0 (for example, "0.0.0.0/0.0.0.0/123.124.125.126"). However, this has the problem that it will block all calls on the private network, so that that there is also a rule necessary for the private network.
Example: Let's say the PBX is running on 192.168.1.2 address, the netmask is 255.255.0.0 and the internal SIP phones have 192.168.x.x addresses. So the first part of the entry will be "192.168.0.0/255.255.0.0/192.168.1.2". This part will take care of the internal phones. Now, if the phone and PBX have to talk to remote phones and servers, then you have added another part to the "IP Routing List". Consider the public IP address is 123.124.125.126(this the IP address provided/assigned by the internet service provider. You can check the public IP using http://whatismyip.com/), then you will have "0.0.0.0/0.0.0.0/123.124.125.126" as the other part of the entry.
Putting it all together, an entry of "192.168.0.0/255.255.0.0/192.168.1.2 0.0.0.0/0.0.0.0/123.124.125.126" will make the PBX serve both internal and remote phones.
In this example, the PBX would not look at the routing presented by the operating system.

