
SSLKEYLOGFILE
Encrypting the TLS traffic between the PBX and HTTP or SIP clients is essential for keeping the communications secure. However when troubleshooting problems this can be a major problem.
Web browsers have a way to log data that is critical for analyzing the traffic to a key log file, usually stored in the environment variable SSLKEYLOGFILE. Why not use that same mechanism for analyzing SIP traffic?
Starting from version 58.3, in the security section of the PBX administrators can set a path for the key logging file, which is written in the format that this SSLKEYLOGFILE uses. This can be read e.g. by Wireshark to display the encrypted content of the connection even in live captures. Once Wireshark can see the SRTP keys, it will also be able to play back SRTP captures.
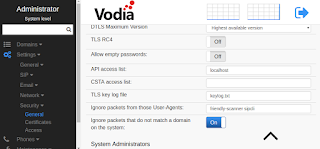
The setting affects connections that are created after hitting the save button. It is not required to restart the PBX, making this useful for debugging encrypted messages in a live system. After turning this off, the PBX will stop writing keys; after restarting the PBX the file will be reset (if the log file is still set).
This feature should also be useful when using external monitoring systems, e.g. voipmonitor. As encryption becomes more and more popular, this will make sure that external live monitoring is still possible.
There are several guides in the Internet that demonstrate how this feature can be used for debugging.

